In late 2016, I replaced my ISP router & modem combination – the BT SmartHub 6 – with separate bits of kit, to give me a little more freedom and something to occasionally tinker with. After a bit of research and bargain hunting, I ended up with:
- Modem – BT Openreach ECI VDSL 1b
- Router – Linksys WRT1200AC
I originally picked up the WRT1200AC for its wireless speed & the ability to use opensource operating systems on it. I ran it from the very beginning with OpenWRT/LEDE, but found it cumbersome to keep it up to date. Upgrading LEDE meant I had to continually reinstall various software packages which didn’t come as standard (igmpproxy for multicast connections for BT YouView etc.), as well as reinstating the config for that software. Whilst I could have written scripts to handle all of this, it felt clunky and not really fit for purpose. You want your router to be almost invisible & rock solid, not something you have to SSH into every couple of weeks.
So, I went hunting for something a little sturdier. I remember reading the excellent The Router Rumble article on Ars Technica where they put a homebrew Linux based router against a number of other contenders, including a Ubiquiti EdgeRouter Pro & a Mikrotik hEX. I had heard nothing but good things about EdgeRouter & Mikrotik kit, so after comparing them bother, I ended up with the EdgeRouter X.
Why did I pick the ER-X? I liked how they handled the Krack vulnerability, which affected WPA2 Wi-Fi networks and clients. Admittedly, both Ubiquiti & Mikrotik handled it well, so I ended up picking the ER-X purely because the CLI was Debian based and relatively closely reflected Cisco kit in terms of commands — Something else to learn.
EdgeRouter X - It's tiny... slightly bigger than a Raspberry Pi maybe?
You may have noticed that this setup has a lack of Wi-Fi connectivity… The great thing about building a home network this way is that you have freedom to mix and match products, and swap bits out when they no longer become fit for purpose. In this instance, it meant I had the luxury of being able to use a Wi-Fi mesh system throughout the house, giving me the ability to actually walk around whilst on WiFi calling and it not cut out as I pass between access points.
Setup (for IPv4)
The initial setup, to fulfil the its role of ‘router’, is pretty easy thanks to the configuration wizard available within the web based UI. Selecting ‘WAN+2LAN’ will allow you to setup your local internal network, as well as enable PPPoE to talk to the modem and be assigned a public IP address. On the first step, for “Internet Connection Type” you should select PPPoE and enter a username of “bthomehub@btbroadband.com” and for password just put a single space (anything is valid as long as it is not blank).
Et voila!
Enabling IPv6
So, BT are IPv6 enabled, which we wish to take advantage. Why? Because we can. The setup for this is a little more hands on than before, but is simple enough that you can paste the commands into the CLI and have it all setup.
Firstly, sudo su to root on the router so that we can make some configuration changes. To configure the PPPoE for IPv6, we set the following:
set interfaces ethernet eth0 pppoe 0 ipv6 enable
set interfaces ethernet eth0 pppoe 0 ipv6 address autoconf
set interfaces ethernet eth0 pppoe 0 ipv6 dup-addr-detect-transmits 1
set interfaces ethernet eth0 pppoe 0 dhcpv6-pd pd 0 prefix-length /56
set interfaces ethernet eth0 pppoe 0 dhcpv6-pd rapid-commit enable
set interfaces ethernet eth0 pppoe 0 dhcpv6-pd prefix-only
For the firewall, we have a couple of things to set. Because an IPv6 address is allocated to each device, we essentially put them directly on the Internet. Not great from a security perspective. So, to limit that risk a little, we are going to set it up so that only established & related connections are allowed, as well as ICMPv6 (ping), and DHCPv6 (so we can be assigned an address). Everything else gets dropped.
set firewall ipv6-name WANv6_LOCAL default-action drop
set firewall ipv6-name WANv6_LOCAL description 'Local network traffic'
set firewall ipv6-name WANv6_LOCAL enable-default-log
set firewall ipv6-name WANv6_LOCAL rule 10 action accept
set firewall ipv6-name WANv6_LOCAL rule 10 description 'Allow established/related sessions'
set firewall ipv6-name WANv6_LOCAL rule 10 state established enable
set firewall ipv6-name WANv6_LOCAL rule 10 state related enable
set firewall ipv6-name WANv6_LOCAL rule 20 action drop
set firewall ipv6-name WANv6_LOCAL rule 20 description 'Drop invalid state'
set firewall ipv6-name WANv6_LOCAL rule 20 state invalid enable
set firewall ipv6-name WANv6_LOCAL rule 30 action accept
set firewall ipv6-name WANv6_LOCAL rule 30 description 'Allow IPv6 icmp'
set firewall ipv6-name WANv6_LOCAL rule 30 protocol icmpv6
set firewall ipv6-name WANv6_LOCAL rule 40 action accept
set firewall ipv6-name WANv6_LOCAL rule 40 description 'allow dhcpv6'
set firewall ipv6-name WANv6_LOCAL rule 40 destination port 546
set firewall ipv6-name WANv6_LOCAL rule 40 protocol udp
set firewall ipv6-name WANv6_LOCAL rule 40 source port 547
set firewall ipv6-name WANv6_LOCAL default-action drop
set firewall ipv6-name WANv6_LOCAL description 'WAN inbound traffic to the router'
set firewall ipv6-name WANv6_IN enable-default-log
set firewall ipv6-name WANv6_IN rule 10 action accept
set firewall ipv6-name WANv6_IN rule 10 description 'Allow established/related sessions'
set firewall ipv6-name WANv6_IN rule 10 state established enable
set firewall ipv6-name WANv6_IN rule 10 state related enable
set firewall ipv6-name WANv6_IN rule 20 action drop
set firewall ipv6-name WANv6_IN rule 20 description 'Drop invalid state'
set firewall ipv6-name WANv6_IN rule 20 state invalid enable
set firewall ipv6-name WANv6_IN rule 30 action accept
set firewall ipv6-name WANv6_IN rule 30 description 'Allow IPv6 icmp'
set firewall ipv6-name WANv6_IN rule 30 protocol icmpv6
set firewall ipv6-name WANv6_IN rule 40 action accept
set firewall ipv6-name WANv6_IN rule 40 description 'allow dhcpv6'
set firewall ipv6-name WANv6_IN rule 40 destination port 546
set firewall ipv6-name WANv6_IN rule 40 protocol udp
set firewall ipv6-name WANv6_IN rule 40 source port 547
set interfaces ethernet eth0 pppoe 0 firewall in ipv6-name WANv6_IN
set interfaces ethernet eth0 pppoe 0 firewall in name WAN_IN
set interfaces ethernet eth0 pppoe 0 firewall local ipv6-name WANv6_LOCAL
set interfaces ethernet eth0 pppoe 0 firewall local name WAN_LOCAL
Next up, we need to enable IPv6 SLAAC (IPv6 Stateless Address Auto Configuration) on our LAN, which is called switch0 if we used the configuration wizard.
set interfaces ethernet eth0 pppoe 0 dhcpv6-pd pd 0 interface switch0 host-address '::1'
set interfaces ethernet eth0 pppoe 0 dhcpv6-pd pd 0 interface switch0 prefix-id '::1'
set interfaces ethernet eth0 pppoe 0 dhcpv6-pd pd 0 interface switch0 service slaac
Finally, lets enable IPv6 on switch0:
set interfaces switch switch0 ipv6 dup-addr-detect-transmits 1
set interfaces switch switch0 ipv6 router-advert cur-hop-limit 64
set interfaces switch switch0 ipv6 router-advert link-mtu 0
set interfaces switch switch0 ipv6 router-advert managed-flag false
set interfaces switch switch0 ipv6 router-advert max-interval 600
set interfaces switch switch0 ipv6 router-advert other-config-flag false
set interfaces switch switch0 ipv6 router-advert prefix '::/64' autonomous-flag true
set interfaces switch switch0 ipv6 router-advert prefix '::/64' on-link-flag true
set interfaces switch switch0 ipv6 router-advert prefix '::/64' valid-lifetime 2592000
set interfaces switch switch0 ipv6 router-advert reachable-time 0
set interfaces switch switch0 ipv6 router-advert retrans-timer 0
set interfaces switch switch0 ipv6 router-advert send-advert true
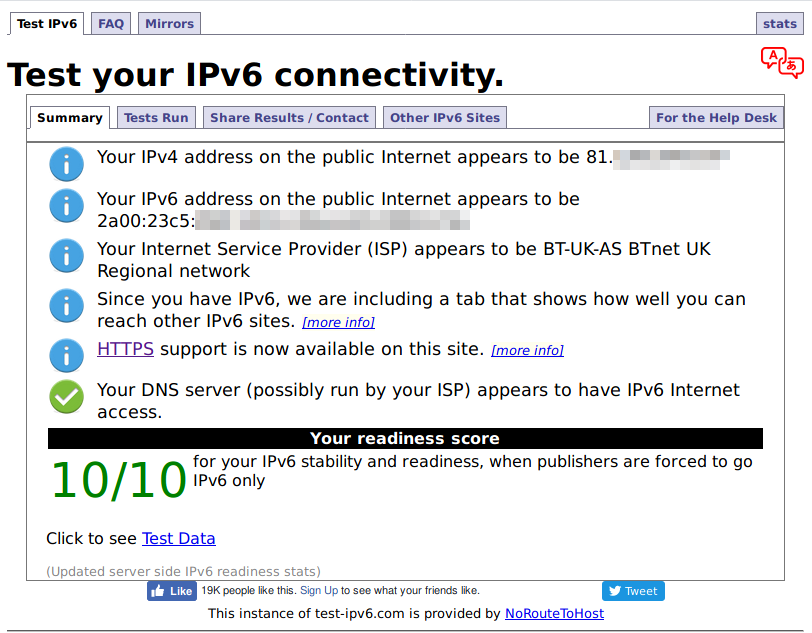
If everything went smoothly, you shouldn’t have any error messages. At this point we can either commit to save the changes, or discard to scrap them. If you commit and everything works as expected (you can check on test-ipv6.com), you can use save to write the changes to the config file so that they persist across reboots.